
Key Takeaways
- SASE offers a unified framework that blends networking and security functions for robust, scalable protection.
- The cloud-native nature of SASE makes it ideal for organizations adopting hybrid work and remote access models.
- Implementing SASE can streamline operations, reduce vendor complexity, and enhance overall security posture.
- An informed approach to SASE adoption includes infrastructure assessment, clear policy definition, and ongoing optimization.
Table of Contents
- Understanding the Shift to SASE
- Key Components of SASE
- Benefits of Adopting SASE
- Real-World Adoption and Impact
- Addressing Hybrid Work Challenges
- Implementing SASE: Steps to Consider
- Conclusion
Understanding the Shift to SASE
Organizations of every size are navigating a complex threat landscape spanning traditional and cloud environments. With cyberattacks continually becoming more sophisticated, relying solely on legacy perimeter-based security is no longer sufficient. Enter Secure Access Service Edge (SASE)—a paradigm that merges networking and security services into one holistic, cloud-driven framework. This powerful shift is redefining how businesses secure their users, data, and applications from any location.
SASE architecture empowers enterprises to deploy network and security controls closer to where users and data reside—across branches, remote offices, and even employee homes. This transformation is managed via the cloud and delivers robust, consistent protection no matter where employees work or which applications they use. By embracing a SASE architecture, organizations gain the agility and resilience needed to stay ahead of evolving cyber threats while streamlining network management.
In addition to risk management, SASE addresses operational challenges arising from remote work and the increased reliance on SaaS applications. With an ever-growing mix of endpoints and third-party services, SASE offers seamless policy enforcement and real-time threat intelligence, providing a vital foundation for today’s digital enterprise.
Key Components of SASE
At its core, SASE fuses several foundational technologies into a globally distributed cloud service:
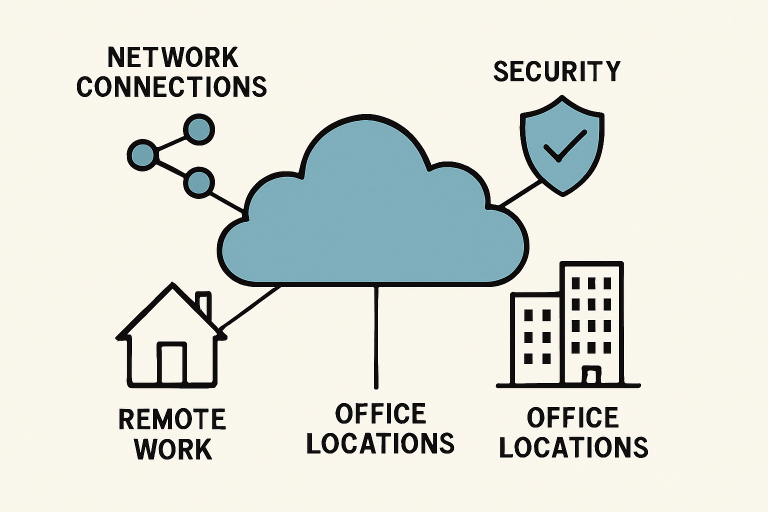
- SD-WAN (Software-Defined Wide Area Network): SD-WAN enables organizations to efficiently and securely connect far-flung locations, eliminating the need for costly private circuits and enabling intelligent traffic routing over any available link.
- Zero Trust Network Access (ZTNA): Zero Trust principles restrict network access based on user identity and context, ensuring that resources are available only to verified users and devices.
- Cloud Access Security Broker (CASB): CASB solutions provide visibility and policy enforcement as users interact with cloud services, helping prevent data leakage and ensure compliance.
- Secure Web Gateway (SWG): SWGs safeguard users by filtering potentially malicious internet content, blocking phishing sites, and enforcing web usage policies across all users.
Each of these pieces works in tandem to eliminate security gaps, reduce attack surfaces, and provide a frictionless, secure user experience.
Benefits of Adopting SASE
SASE’s unified approach translates to significant advantages for modern organizations, including:
- Enhanced Security: The integration of multiple security services ensures end-to-end protection from a single pane of glass, reducing the risks posed by shadow IT and fragmented policies.
- Reduced Complexity: Moving to a single-vendor or tightly integrated platform means fewer tools to manage, less duplication, and simplified troubleshooting.
- Improved Performance: Cloud-based SASE infrastructure brings security and networking services closer to the end user, dramatically cutting latency for web-based and SaaS apps.
- Scalability: SASE solutions scale on demand, supporting business growth, seasonal surges, or rapid expansion to new locations without the traditional infrastructure headaches.
Real-World Adoption and Impact
Enterprises across the globe are turning to SASE to rationalize sprawling security stacks and adapt to hybrid work. Research reports that 75% of companies consider vendor consolidation a priority, with SASE emerging as the linchpin of that effort. Consolidated security not only cuts costs but clarifies responsibility, making gaps easier to spot and close.
For example, leading financial institutions and healthcare providers—both heavily regulated sectors—have embraced SASE for its ability to provide auditable, policy-driven control mechanisms while still supporting a distributed, mobile workforce. The security architecture allows these organizations to make real progress on zero-trust and continuous compliance journeys.
Addressing Hybrid Work Challenges
The widespread shift to remote and hybrid working models presents unique data protection and access control challenges. More connections outside the traditional network perimeter increase the risk of unauthorized access, shadow IT, and sensitive information leakage. As BizTech Magazine explains, SASE (Secure Access Service Edge) is increasingly essential for distributed and hybrid work environments, as it is purpose-built to secure access from any device, over any network, in any location—protecting remote workers just as thoroughly as those in the office.
Implementing SASE: Steps to Consider
1. Assess Current Infrastructure
Start by cataloguing your present networking and security landscape, paying special attention to legacy appliances, shadow IT, and current cloud usage patterns. Pinpoint operational and security pain points that SASE can address most effectively.
2. Define Security Policies
Develop comprehensive guidelines in line with business objectives, user roles, and applicable regulatory requirements. SASE adoption is also an opportunity to refresh legacy access controls and align your security stack with zero-trust principles.
3. Select a Trusted Provider
Work with a SASE partner that offers full-stack services, transparent integrations, and proven experience supporting organizations with similar profiles.
4. Plan for Integration
Carefully map out how SASE components will coexist and interoperate with your existing systems. Migrate gradually, starting with the most critical users or applications, to minimize disruption.
5. Monitor and Optimize
Success in a SASE environment depends on constant performance monitoring, user feedback, and regular policy updates. Use usage analytics to identify bottlenecks and opportunities for improvement as your environment evolves.
Conclusion
The move to SASE is more than a security upgrade—it’s a strategic choice for digital transformation. As organizations grapple with increasingly complex cyber threats, distributed teams, and a need for greater business agility, SASE delivers integrated security and networking that adapts as quickly as today’s enterprise demands. By adopting SASE deliberately, businesses can protect sensitive assets, simplify management, and unlock a more flexible, resilient future.
